
Probing through every open port is practically the first step hackers take in order to prepare their attack. And in order to work, one is required to keep their port open but at the same time, they are threatened by the fear of hackers. Therefore, one must learn to secure their ports even if they are open. In this post, we will discuss about security penetration testing of SSH which is also known as Secure Shell.
1. Introduction to SSH
The SSH protocol also stated to as Secure Shell is a technique for secure and reliable remote login from one computer to another. It offers several options for strong authentication, as it protects the connections and communications/security and integrity with strong encryption. It is a secure alternative to the non-protected login protocols (such as telnet, rlogin) and insecure file transfer methods (such as FTP).
2. SSH Installation
It very easy to install and configure ssh service, we can directly install ssh service by using the openssh-server package from ubuntu repo. To install any service you must have root privilege account and then follow the given below command.
apt install openssh-serverwhen you will execute above command it will extract the package the install the default configure on the host machine. you can check open port with the help of netstat command on the host machine.
3. SSH Port Scanning
If you don’t have direct access to the host machine, use nmap to remotely identify the port state that is considered to be the initial step of the security penetration testing. Here we’re going to use Kali Linux to perform a penetration testing.
So, to identify an open port on a remote network, we will use a version scan of the nmap that will not only identify an open port but will also perform a banner grabbing that shows the installed version of the service.
nmap -sV -p 22 192.168.2.128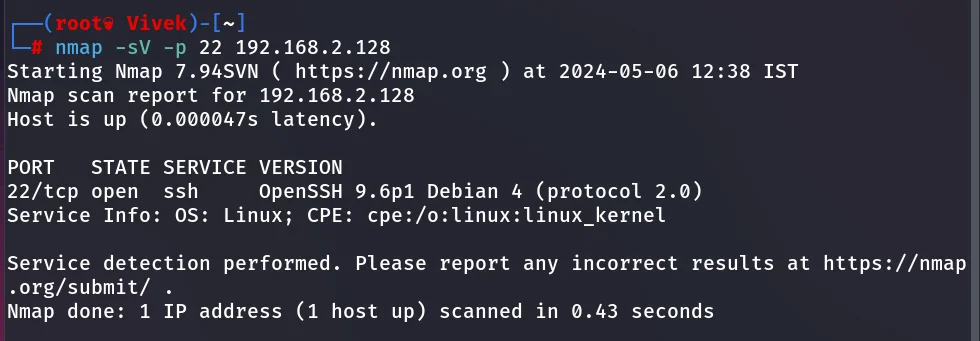
4. Methods to Connect SSH
i. Terminal Command (Linux)
Now execute the following command to access the ssh shell of the remote machine as an authorized user.
Username: NS3EDU
Password: 123
ssh [email protected]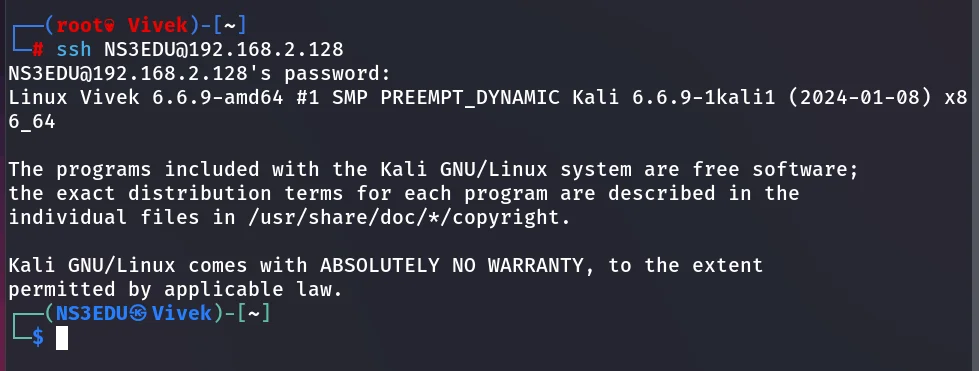
ii. Putty (Windows)
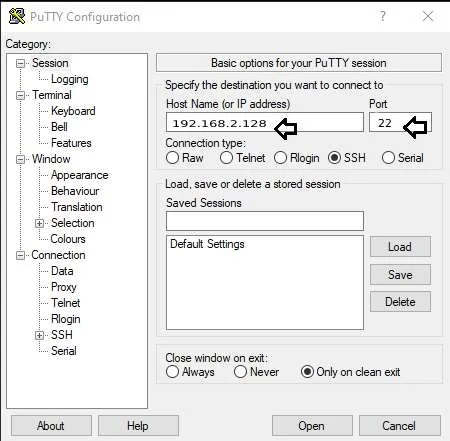
Step1: Install putty.exe and run it, then enter the HOST IP address <192.168.2.128> and port <22>, also choose to connect ssh.
Step2: To establish a connection between the client and the server, a putty session will be generated that requires a login credential.
Username: NS3EDU
Password: 123
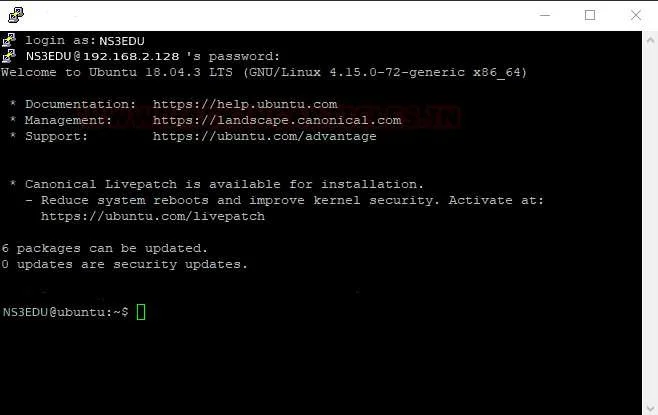
5. Port Redirection
By default, ssh listen on port 22 which means if the attacker identifies port 22 is open then he can try attacks on port 22 in order to connect with the host machine. Therefore, a system admin chooses Port redirection or Port mapping by changing its default port to others in order to receive the connection request from the authorized network.
Follow the below steps for port redirection:
Step1: Edit the sshd_config from inside the /etc/sshd using the editor.
nano/etc/ssh/sshd_config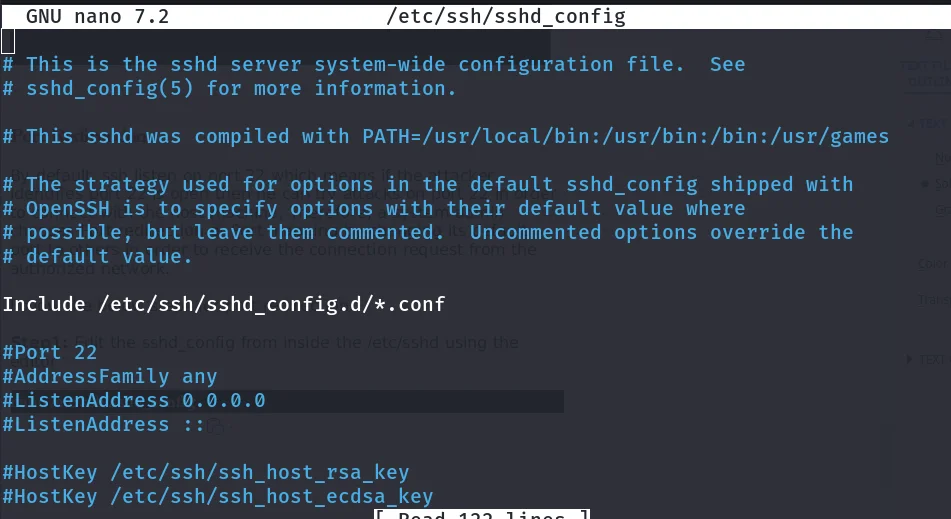
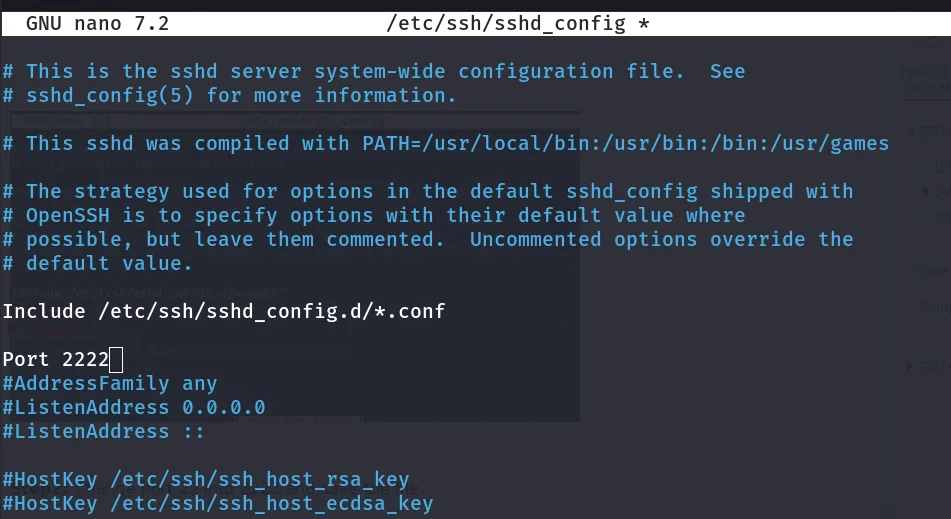
Step2: Change port 22 into 2222 and save the file.
Step3: Then restart ssh.
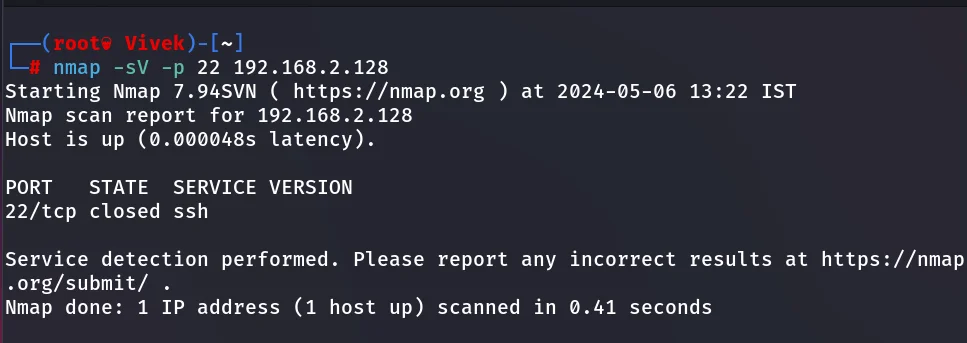
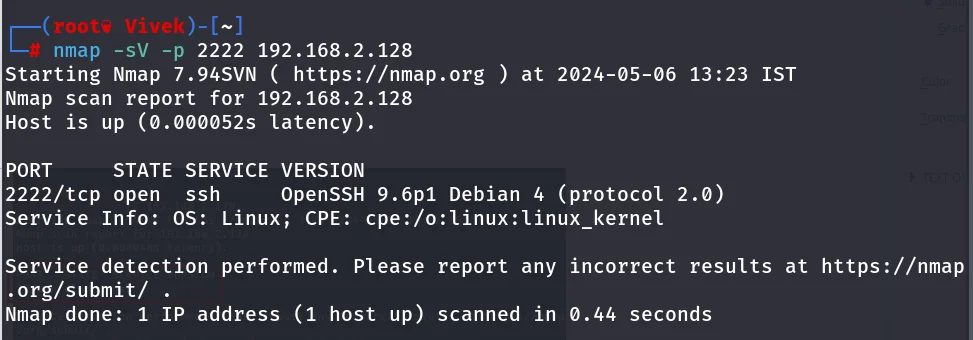
Port Redirection Testing
Thus, when we have run the scan on port 22, it has shown port state CLOSE for ssh whereas port 2222 OPEN for ssh which can be seen the given image.
6. Establish SSH connection using RSA key
Strong passwords don’t seem to be decent to secure the server because a brute force attack can crack them. That’s why you need an additional security method to secure the SSH server.
Security penetration testing & SSH key pairs is another necessary feature to authenticate clients to the server. It consists of a long string of characters: a public and a private key. You can place the public key on the server and private key on the client machine and unlock the server by connecting the private key of the client machine. Once the keys match up, the system permits you to automatically establish an SSH session without the need to type in a password.
Ssh-keygen is a tool for creating new authentication key pairs for SSH. Such key pairs are used for automating logins, single sign-on, and for authenticating hosts.
Thus, we will follow the steps for generating a key pair for authenticated connection and security penetration testing.
Step1: Run the given command to generate an ssh key pair (id_rsa and id_rsa.pub) on the host machine Ubuntu.
ssh-keygen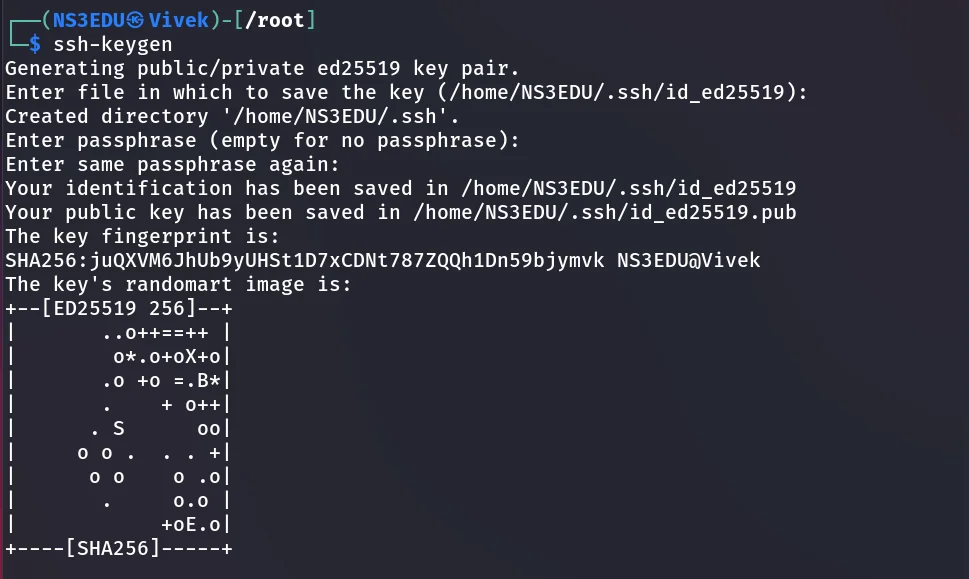

Step2: Same should be done on the client machine which is authorized to establish the connection with the host machine (ubuntu).
Step3: Once the ssh key pair (id_rsa and id_rsa.pub) get generated then rename the id_rsa.pub into authorized_keys as show in the given image.
ssh-keygencd.sshlscat id_rsa.pub > authorized_keys
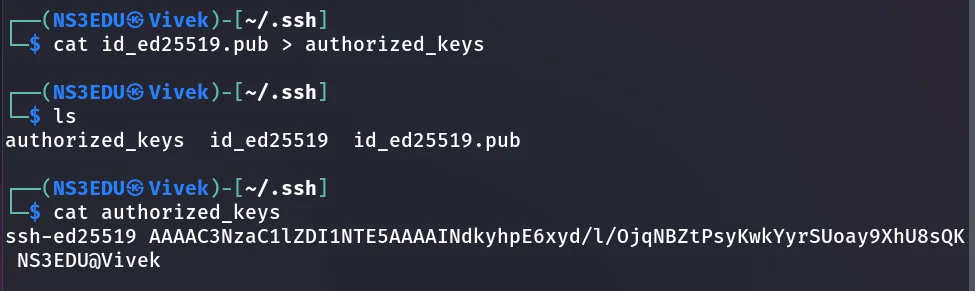
Step4: Share the authorized_keys with the host machine by copying it into the .ssh directory.
Step5: Edit the sshd_config from inside the /etc/sshd using the editor
nano/etc/ssh/sshd_config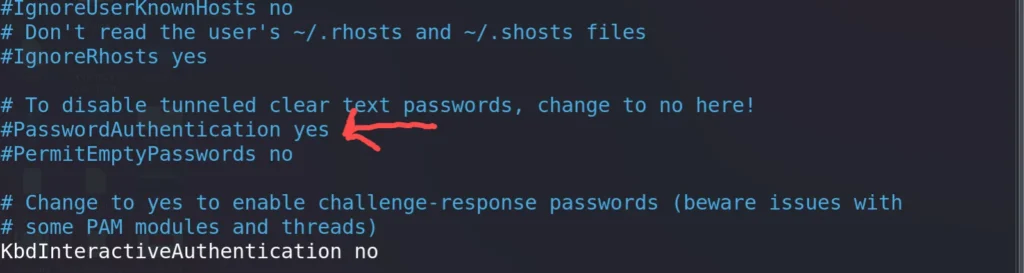
Step6: Enable the “passwordauthentication no” comment
As a result of only the authorized machine which rsa key can establish a connection with the host machine without using password.
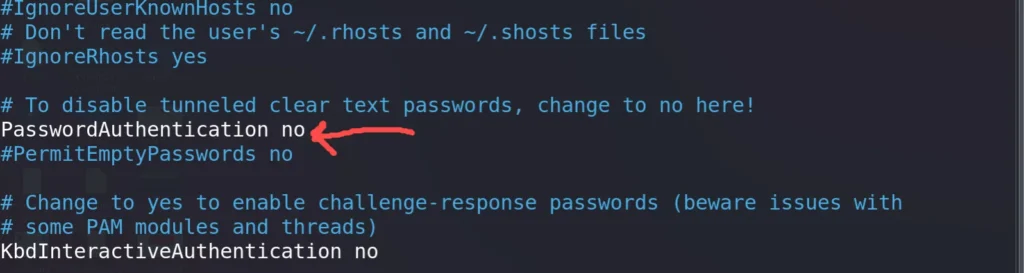
Now if you need to connect to the ssh server using your password username, the server will drop your connection request because it will authenticate the request that has authorized key.
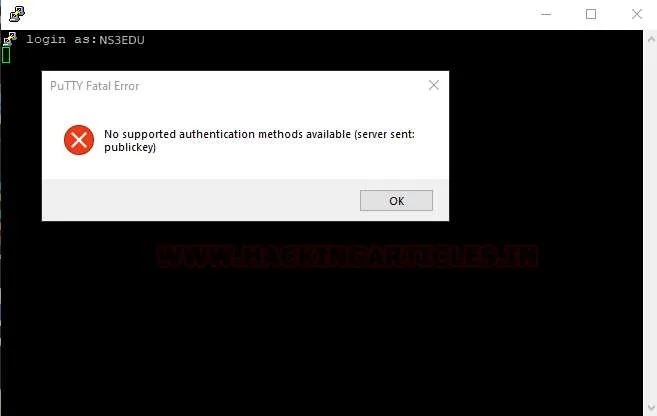
Step7: Copy the id_rsa key from Kali Linux to the windows machine, to established connection using authorized keys on the windows machine.
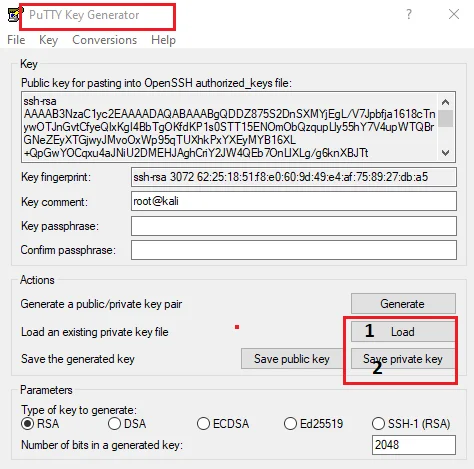
Step8: Install puttygen.exe
Step 9: Run puttygen.exe and load the id_rsa and “save as key” named as Key
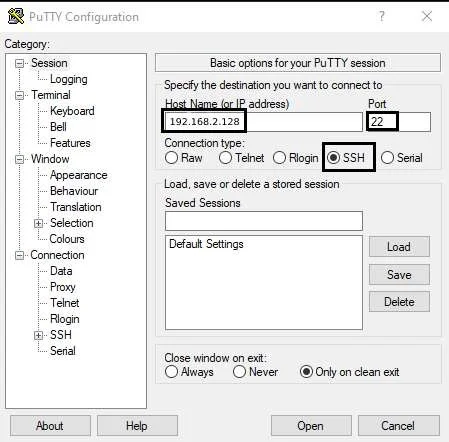
Step10: Use putty.exe to connect with the host machine by entering hostname 192.168.2.128 and port 22.
Step11: Navigate to SSH >auth and browse the key private key that you have saved as mention in step 9.
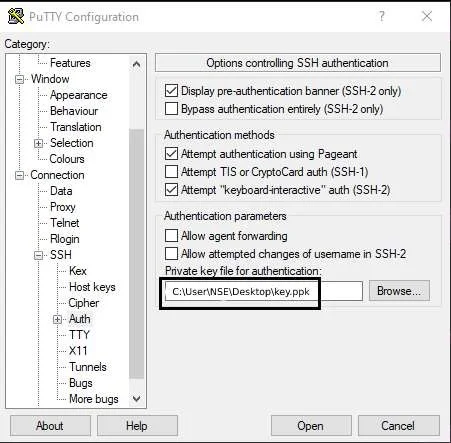
This will establish an ssh connection between windows client and server without using a password.
7. SSH Password cracking
We can test a brute force attack on ssh for guessing the password or to test threshold policy while performing penetration testing on SSH. It requires a dictionary for username list and password list, here we have username dictionary “user.txt” and password list named “pass.txt” to perform the brute force attack with the help of hydra.
hydra -L user.txt -P pass.txt 192.168.1.103 ssh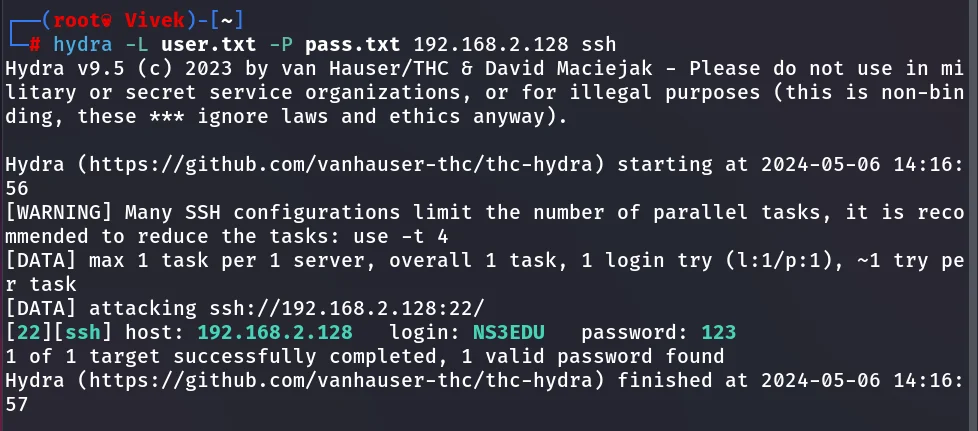
As a result, you can observe that the host machine has no defence against brute force attack, and we were able to obtain ssh credential.
Conclusion:
In this post, we try to discuss the possible way to perform penetration testing against such a scenario.
