
Palo Alto Firewall Interface offers diverse interface types, each serving distinct network functions.
Here are some common Palo Alto firewall interface types:
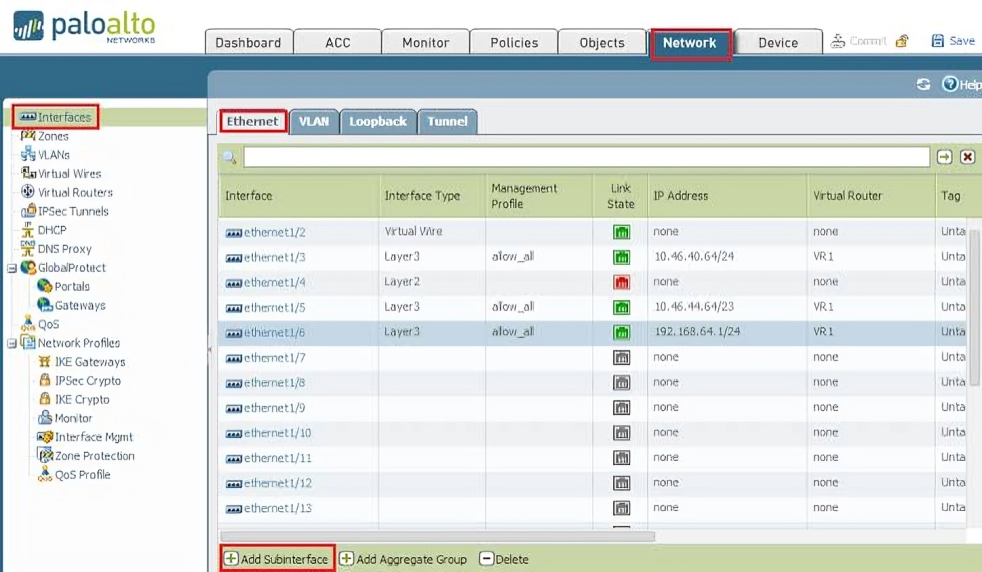
Management Interface: Used for device management, including configuration and monitoring. Typically accessed through the web-based management interface (WebUI) or CLI.
Ethernet Interfaces: Used for connecting to the network and handling data traffic. Can be configured as Layer 2 or Layer 3 interfaces.
Aggregate Ethernet Interfaces: Combines multiple physical interfaces into a logical interface for increased bandwidth.
Loopback Interfaces: Virtual interfaces used for management or routing purposes.
Virtual Wire Interfaces: Used in transparent mode to connect two networks without IP address changes.
GRE (Generic Routing Encapsulation) Tunnels: Used to encapsulate a variety of network layer protocols. Commonly used for creating secure site-to-site connections.
IPsec Tunnels: Used for encrypted communication between two networks.
VLAN Sub-interfaces: Allows the firewall to participate in VLAN trunking.
HA (High Availability) Interfaces: Used for communication between high availability peers.
Tap Interfaces: Monitors traffic without affecting its flow and useful for network analysis or monitoring.
Virtual Router Interfaces: Used to connect different virtual routers within the firewall.
SSL Decryption Mirroring Interface: Used to mirror SSL-decrypted traffic for analysis.
Log Collection Interfaces: Dedicated interfaces for forwarding logs to external log collectors.
Understanding these interface types is crucial for configuring Palo Alto firewalls to meet specific network requirements. Depending on the deployment scenario and network architecture, different interface types will be utilized to ensure proper traffic handling and security enforcement.
