
In computer networking, one of the fundamental challenges is to maintain a stable and efficient communication path between devices in a local area network (LAN). This task becomes more complex when there are redundant links present, which can lead to loops and packet collisions. Spanning Tree Protocol (STP) is a crucial mechanism designed to address this issue by ensuring loop-free network topologies. In this blog, we will delve into the concept of Spanning Tree, its working, and its significance in modern network infrastructures.
What is Spanning Tree Protocol?
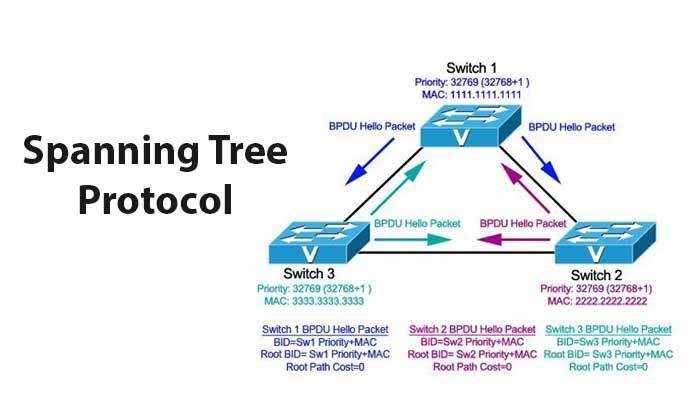
Spanning Tree is a layer 2 protocol, defined by the IEEE 802.1D standard, which aims to prevent loops in Ethernet networks. When multiple paths exist between network switches and bridges, loops can occur, causing broadcast storms and network congestion. STP strategically disables some of these redundant paths, creating a tree-like structure, where one switch is the root bridge and all other switches connect to it.
How Does Spanning Tree Protocol Work?
Electing the Root Bridge: The first step in STP operation is the election of the root bridge. All switches in the network competes to become the root bridge based on their Bridge ID (BID), which comprises a combination of the switch’s priority and MAC address. The switch with the lowest BID wins the election and becomes the root bridge.
Selecting the Root Ports: Each non-root bridge determines the shortest path to the root bridge. The port through which the bridge can reach the root bridge with the lowest path cost is designated as the root port.
Choosing Designated Ports: On each network segment, one port with the lowest path cost to the root bridge is selected as the designated port. The designated port is responsible for forwarding traffic towards the root bridge.
Blocking Redundant Ports: Any ports that are not selected as root ports or designated ports are put into a blocking state. These ports are effectively disabled to avoid loop formation.
Detecting Failures: Spanning Tree continuously monitors the network for changes. If a link fails or a new switch is introduced, STP recalculates the spanning tree and adjusts the port states accordingly to maintain a loop-free topology.
Benefits of Spanning Tree Protocol:
Loop Prevention: The primary purpose of STP is to prevent network loops, which can cause broadcast storms and degrade network performance.
Redundancy: Although STP disables some redundant links, it ensures that backup paths are available in case of link failures, ensuring network reliability.
Plug-and-Play: STP automatically adapts to network changes, making it easy to add or remove switches and links without manual reconfiguration.
Efficient Traffic Flow: By selecting the shortest path to the root bridge, STP optimizes traffic flow and reduces latency in the network.
STP Variants: Over the years, several improvements and variants of STP have been developed to enhance its functionality. Some of the popular ones include:
Rapid Spanning Tree Protocol (RSTP): IEEE 802.1w introduced RSTP, which significantly reduces the convergence time after network changes.
Multiple Spanning Tree Protocol (MSTP): MSTP, defined by IEEE 802.1s, allows for the creation of multiple spanning trees to optimize network performance in larger environments.
Per-VLAN Spanning Tree Protocol (PVSTP): Cisco’s proprietary PVSTP enables STP to operate separately
for each VLAN, providing better control over redundant links in a VLAN-based network.
Conclusion:
Spanning Tree Protocol remains a critical technology in modern network infrastructures, ensuring stable and efficient communication by preventing loops. Its ability to adapt to network changes, handle redundancy, and maintain a loop-free topology makes it an essential part of building reliable and robust LANs. As networking technologies continue to evolve, STP’s variants and alternatives will play a vital role in creating efficient and resilient networks that power our interconnected world.
